Unlocking Business Success: Digital Experience Monitoring is a key
February 23, 2024
RIP BSM, and the coming showdown
March 14, 2024xTend for discovery
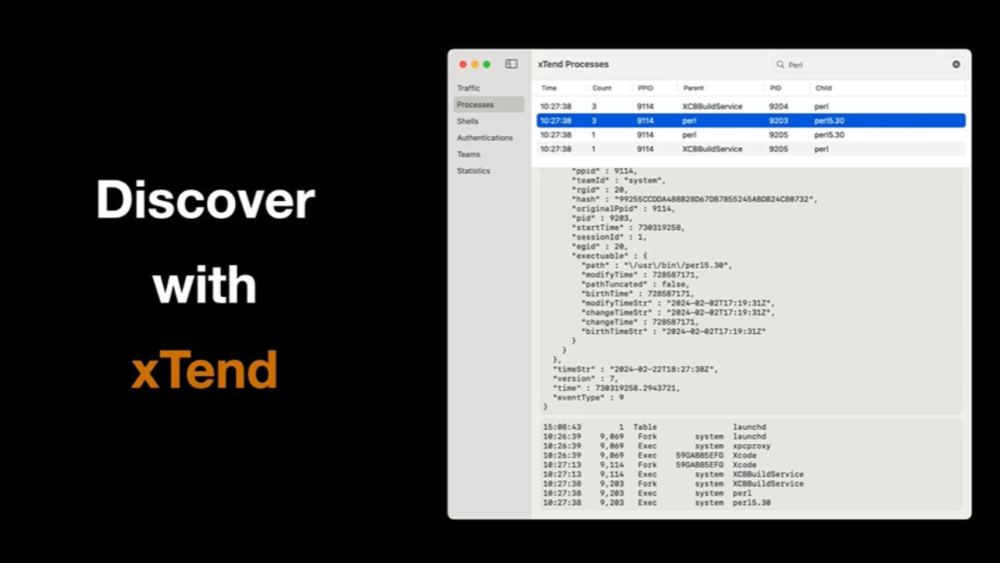
I love using xTend to discover what is happening on my Mac that is invisible without a tool like this.
Sometimes, it can be a bit surprising to know what is happening as shown in this video 😄:
Most of the activity that happens on your computer – programs being run, network connections being initiated – is never directly visible to you.
Sometimes, I watch for all new programs, but often I leave separate xTend windows open with the Processes tab selected and the words “update”, “perl”, or “prot” (for “protect”) in the search fields to spot programs being run with those strings in their names.
Updates
In the screenshot below, xTend is looking for “update” programs running this morning (red arrow points to the search field). It was a busy morning for software updates.
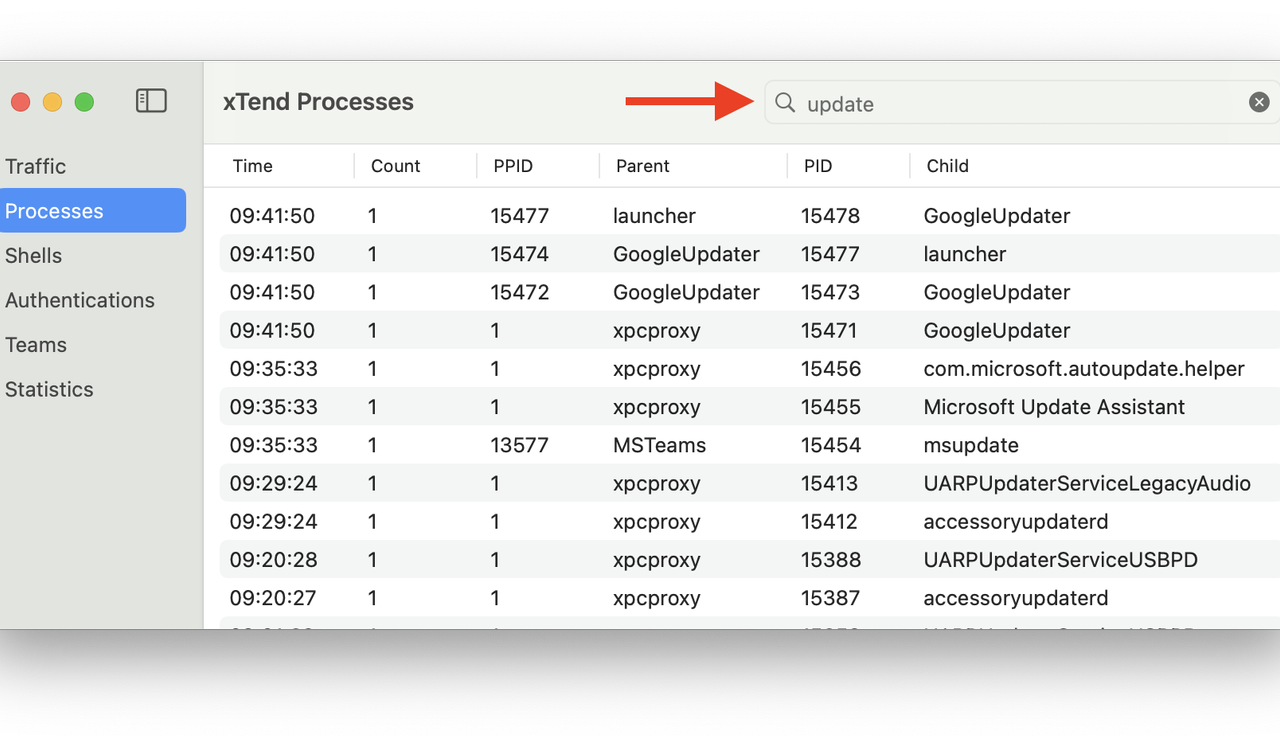
Searching for “updates”
Sometimes, when I see a program that catches my eye, I will pivot to the Traffic tab to look for related network activity. In the figure below, I have selected one of those GoogleUpdater programs calling home. In the bottom pane we see some of the details about this connection, including the full URL queried and arguments passed to it (red box).
Note that this is an encrypted connection, so your typical network monitor will not see the web hostname and certainly not the full URL. And, of course, your network monitor would have no idea what program initiated the connection.
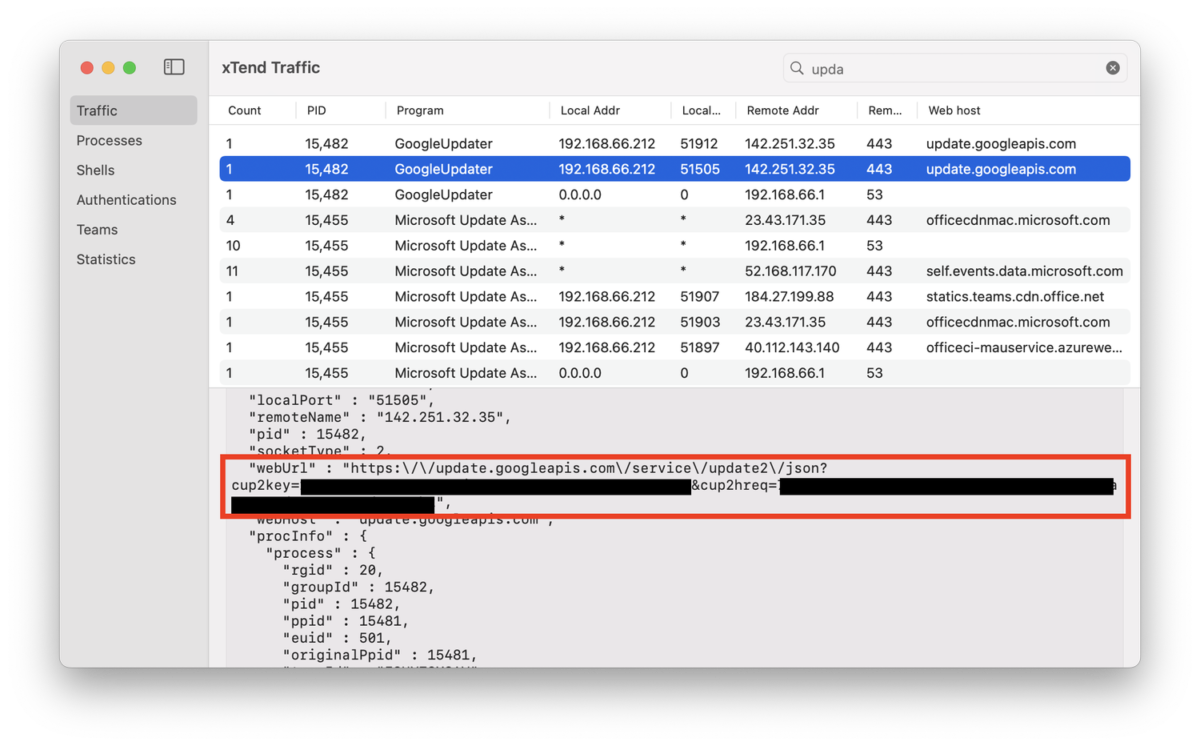
GoogleUpdater calling home (arguments redacted)
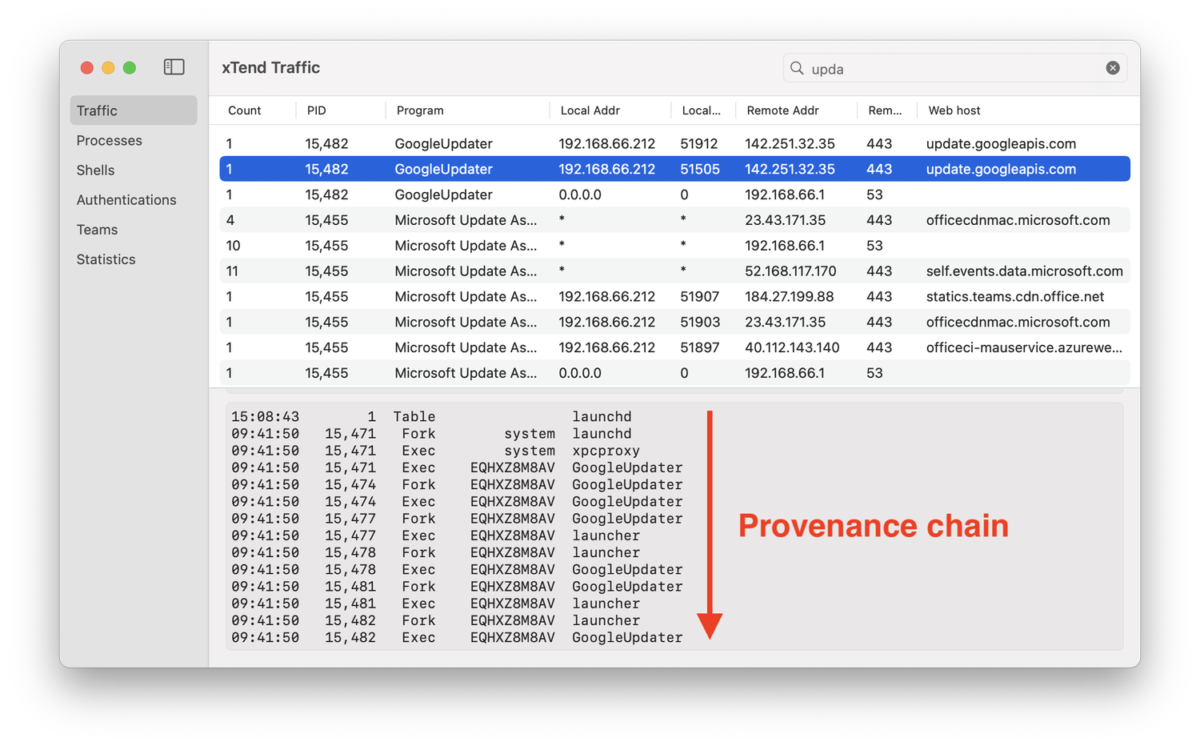
Scrolling to the bottom of the details section we see the provenance chain that led to the program initiating the connection (the process at the bottom of the list). In the provenance chain we see a sequence of fork() and exec() calls with GoogleUpdater recursively calling itself repeatedly.
Provenance chain to GoogleUpdater program initiating the connection
XProtect
XProtect is Apple’s built-in antivirus technology. In the xTend window keeping an eye out for “prot”, I see every time Apple fires off XProtect to protect my system. I also enjoy looking at the names Apple gives the various malware systems.
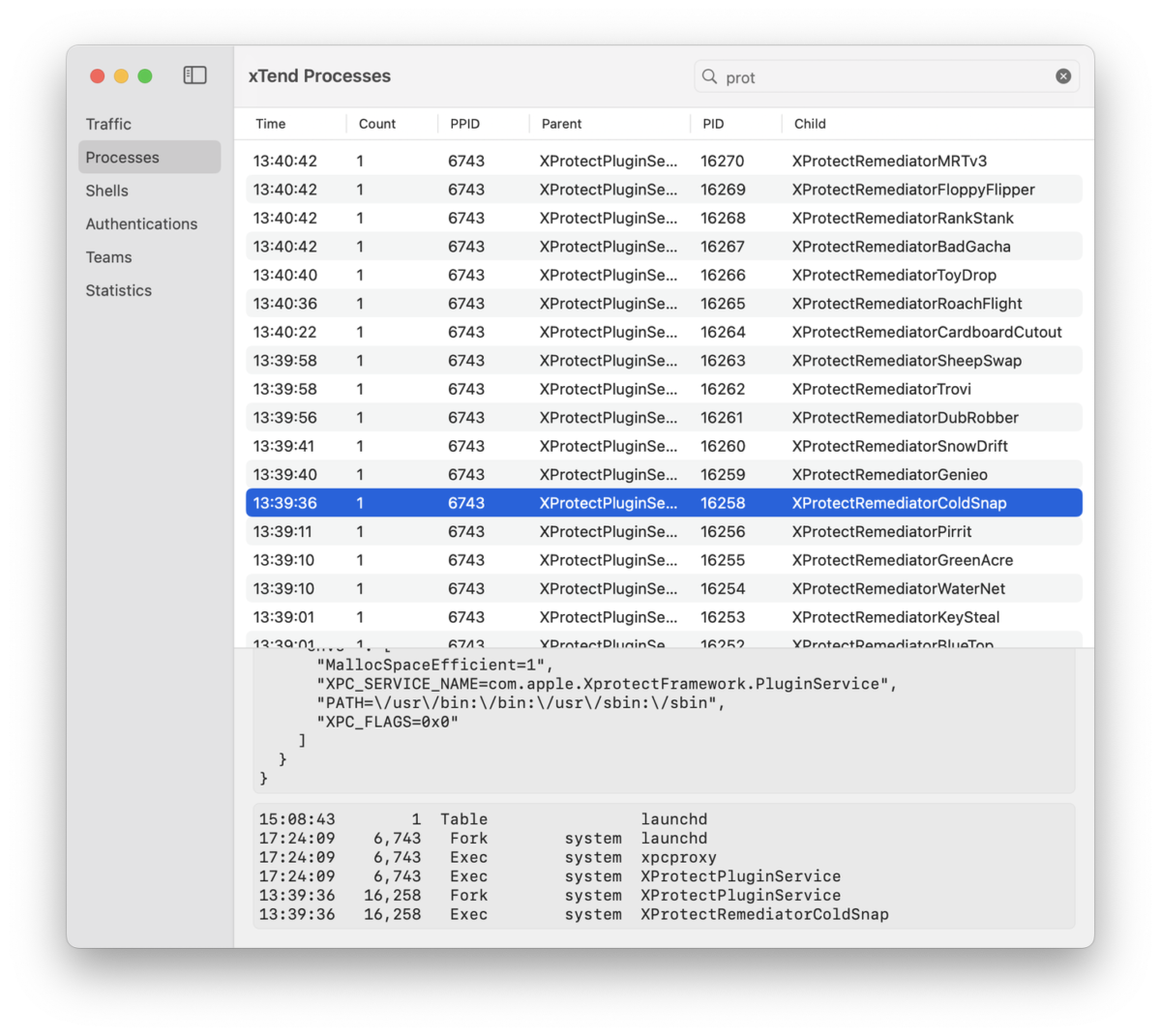
xTend keeping an eye on XProtect keeping an eye on my Mac
Perl
In the video above, I show how I discovered that Xcode uses perl behind the scenes.
Below is one of the screenshots I captured for the video. xTend provides all the arguments and environment variables passed to the program. The red box show the path to the perl program being called.
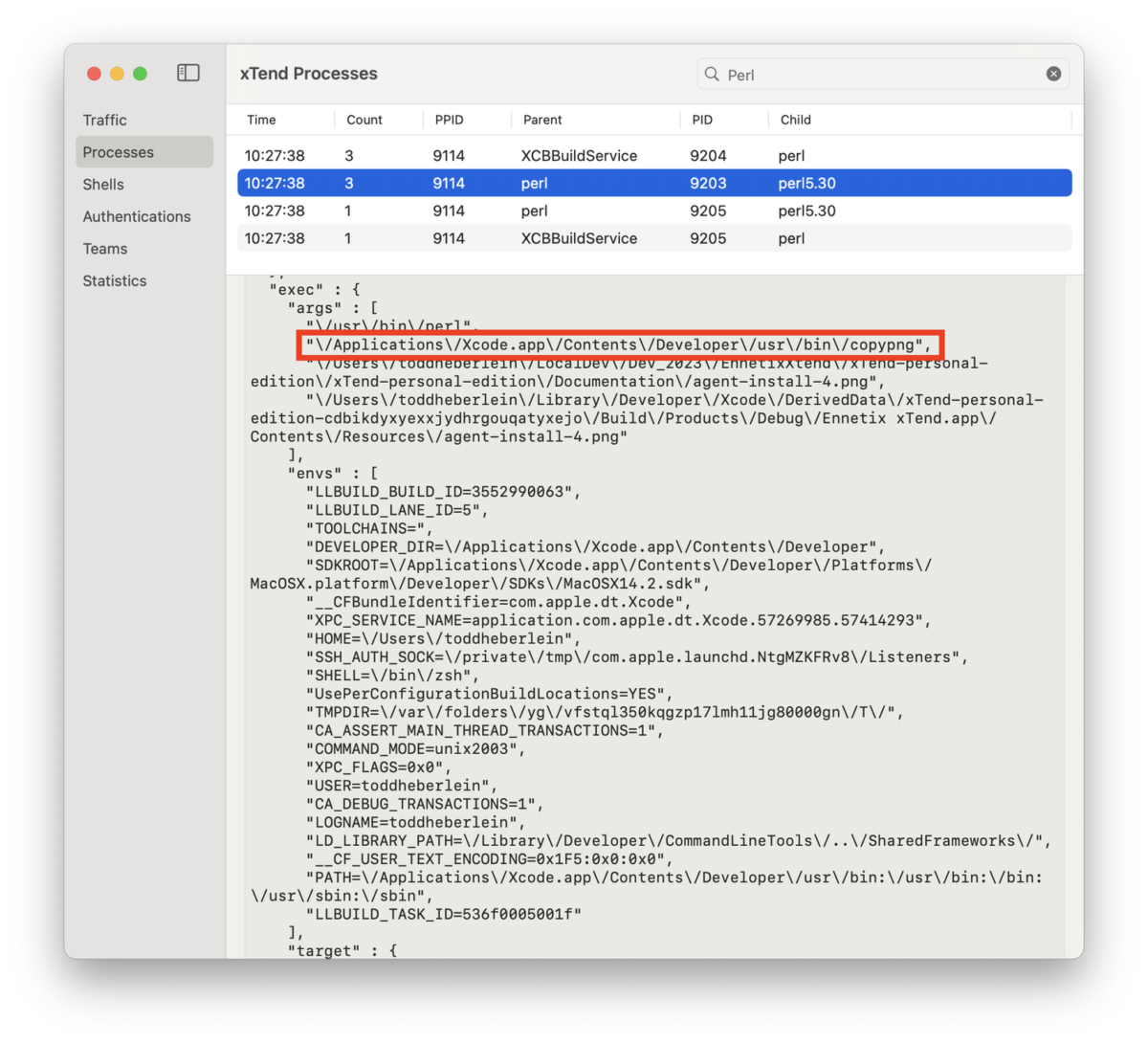
Path to the perl program
Using the path, I took a look at the perl program to see what it was doing. Below are the comments from the beginning of that perl program. If you are curious, you can examine the details for the program on your own computer.
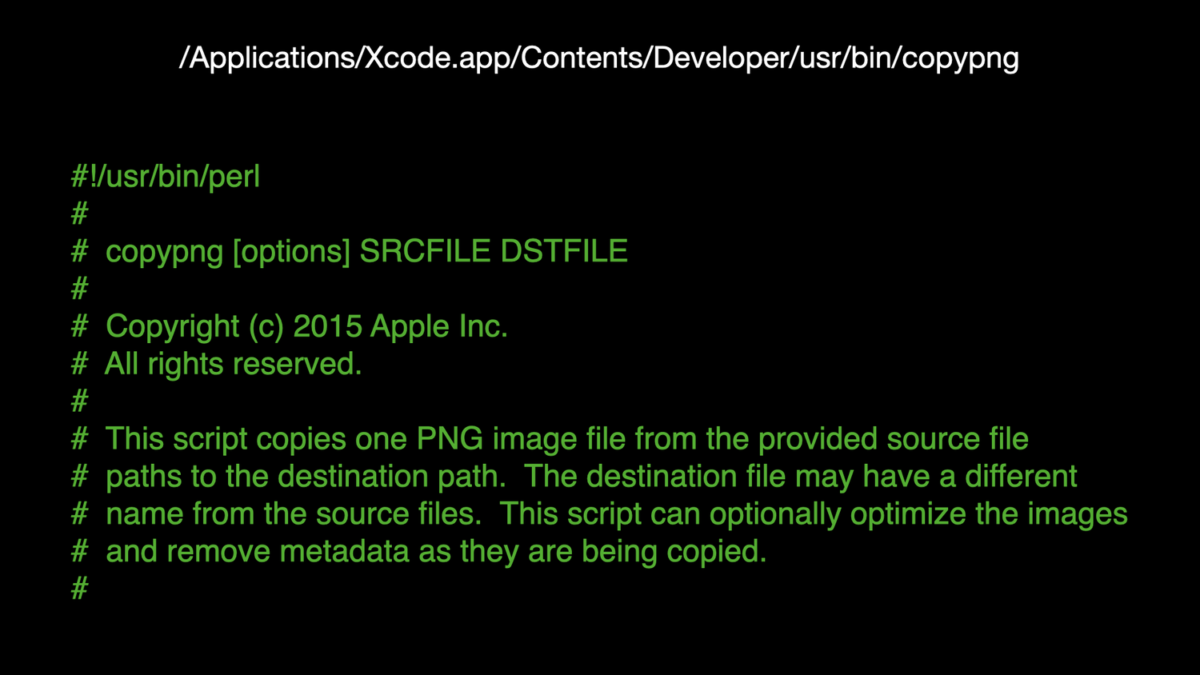
Beginning of perl program Xcode calls
For those who want to know
If you are a computer scientist, security analysts, or just a curious person interested in learning what goes on behind the scenes on your computer, check out xTend in the Mac App Store.