
UEBA for Improving Network Performance and Saving Money
November 8, 2023
Achieving Strong Coordination Between ITOps and SecOps via a Unified AIOps Platform
December 6, 2023Brief History of Networking: Part 2
Firewall: From First Implementation to Today’s Intelligent Systems
The first version of an elementary filtering firewall, called a cut-through bridge, was designed and prototyped in the Computer Networks Laboratory at the University of California, Davis, in 1988. It was built by graduate student Conrad Kwok, under my supervision. I presented this work at the 1989 IEEE International Conference on Communications. Later, we published this work in a leading journal, the IEEE Transactions on Communications.
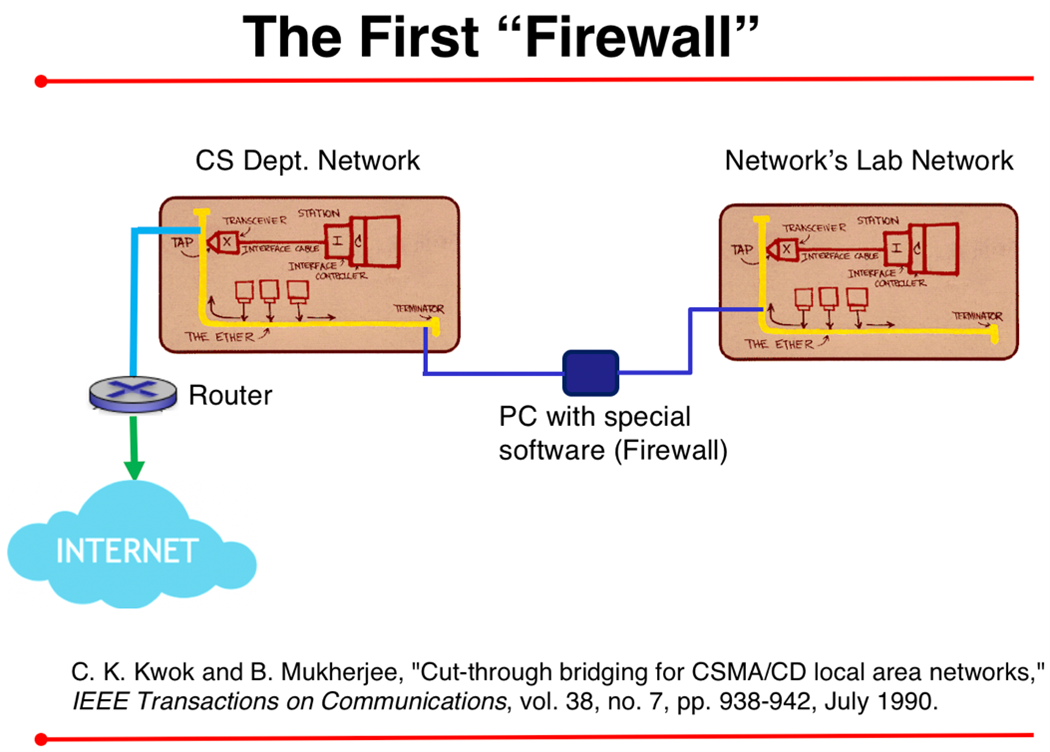
I had joined UC Davis in 1987 as an assistant professor (and a fresh PhD graduate) with background in computer networking. Internet connectivity in enterprises those days was based on coaxial-cable-based Ethernet, deployed as a Carrier-Sense Multiple Access with Collision Detection (CSMA/CD) Local Area Network (LAN). (This was before switched Ethernet or wireless/cellular networks.)
My department (Computer Science) had an Ethernet cable coming from the campus Network Operations Center (NOC). One could connect several Ethernet segments by (passive) repeaters to create a larger Ethernet LAN, which was necessary to increase the network’s geographical coverage. But all of these segments would be part of a larger “collision domain”. As a result, on my Networks Lab Ethernet segment, all other traffic not relevant to my lab would also show up. This would lead to more collisions of Ethernet frames, and lower the effective network throughput.
I wanted to isolate my Networks Lab traffic, so that traffic between machines in my lab stayed inside the Ethernet segment of my lab; also, from the Computer Science Department LAN, only the traffic destined to my lab would show up on my Lab’s Ethernet segment.
To achieve this, we designed and implemented a “bridge” to serve as a “filtering firewall”. Specifically, we took a then state-of-the-art personal computer (IBM PC/RT); put into it two Network Interface Cards (which cost a whopping $995.00 each those days!); connected one of the NICs to the CS Department LAN segment; connected the other NIC to the Networks Lab segment (see Figure); and designed and wrote the software to perform the filtering operations. Briefly, the software learns which destination is on which side of the bridge, and acts accordingly. For details, please see “Cut-through bridging for CSMA/CD local area networks.”
Since this device operated on Ethernet segments, it was a classical Layer-2 bridge. Our design included the “cut-through” property as well, i.e., when the bridge is processing an Ethernet frame, noting that the destination address is at the beginning of the frame, the bridge can decide rather quickly if the frame should be passed on to the other side (and not have to wait until the entire Ethernet frame has been received by the bridge). Thus, the bridge’s throughput – on how fast it can process Ethernet frames – could be highly increased.
As a junior faculty, I was thrilled with this innovation, and published about it. Little did we know three decades back that that such a device (with enhancements) would become a major security tool by blocking network attacks, and firewalls would become a $5-billion-a-year market. About five years after we published this work, I was approached by some lawyers representing a company which was in dispute with another company regarding ownership of some firewall patents. After learning about our work, they decided that neither could claim the first firewall because I had built it first and published about it even though I had not used the term firewall.
Our first firewall, built over 30 years back, was rather elementary (as most first designs are), e.g., it has only two (homogeneous) Ethernet ports, but its cut-through property was quite advanced. Today, firewalls are all-powerful, supporting many heterogenous ports; operating at different levels of the protocol hierarchy; allowing sophisticated filtering rules; serving as a major tool for security and threat intelligence; adapting and self-learning using Artificial Intelligence (AI) techniques; and becoming even more powerful. Several such characteristics (and more) are part of a modern breed of devices, called Intrusion Prevention Systems (IPSs). In fact, IPSs can be combined with Intrusion Detection Systems (IDSs), which we covered in an earlier blog, to deploy powerful IDS/IPS systems.
Several important and relevant characteristics of IDS/IPS are incorporated in xVisor, the AIOps platform from Ennetix. For more information, please visit https://ennetix.com
About the author
Prof. Dr. Bis Mukherjee, Founder and President, Ennetix (also Distinguished Professor, UC Davis); Ph.D., Electrical Engineering, University of Washington, Seattle; B.Tech. (Hons.), Electronics Engineering, Indian Institute of Technology, Kharagpur. Acknowledged authority in pioneering network technologies for 35+ years. His pioneering contributions in the networking world include, first design/proposal/prototype for:
- Network Intrusion Detection System (1990)
- Firewall (1989)
- Dynamic bandwidth allocation for EPON/FTTH (2002)
- Optical-wireless integration (2007), now 5G Fronthaul
References
C. K. Kwok and B. Mukherjee, “Cut-through bridging for CSMA/CD local area networks,” IEEE Transactions on Communications, vol. 38, no. 7, pp. 938-942, July 1990.
Biswanath Mukherjee, L. Todd Heberlein, and Karl N. Levitt, “Network intrusion detection,” IEEE Network, vol. 8, no. 3, pp. 26-41, May/June 1994.












