
xTend Your Visibility into Your Mac (or any Computer)
August 17, 2023
Situational Awareness:”You Know What You Know”
November 8, 2023Distributed Denial of Service (DDoS) is a major threat to any enterprise. A DDoS attack’s goal is to overwhelm the enterprise’s IT infrastructures (specifically servers) by sending huge numbers of junk traffic requests and hampering legitimate service requests. On October 10, 2023, Google reported that it “mitigated the largest DDoS attack to date, peaking above 398 million requests per second (rps)”. Our case study presents DDoS activities on Enterprise A’s DNS servers. Enterprise A’s DNS servers are visible from xVisor’s Security Dashboard (Figure 1). The activities cover the time window from 10:30 a.m. until 4:30 p.m. on August 15, 2023. The focus is on DNS traffic seen from the Internet Client’s perspective. It shows how attackers leveraged Enterprise A’s DNS servers (as a resource) to attack computers across the Internet.
1. View of Top DNS Servers by Traffic Rate
Figure 1 shows xVisor’s Security Dashboard with the DNS tab selected (1). The focus is on Internet Clients (2), and the addresses are sorted by DNS queries/transactions per second (TPS) (3). For example, the top client/victim (explanation below) is generating queries of 34 TPS. If this activity is sustained for an hour, it would resolve to 122,400 DNS queries.
Many of these top client addresses are flagged by both Threat Intelligence feeds (4) and their behavior (5) (based on xVisor’s Machine Learning models). A common giveaway for DDoS over DNS is high query rates reported for domains that do not belong to the enterprise. In this example, we see high, repeated query rates for sl (Sierra Leone), collectd.org, and higi.com (6).
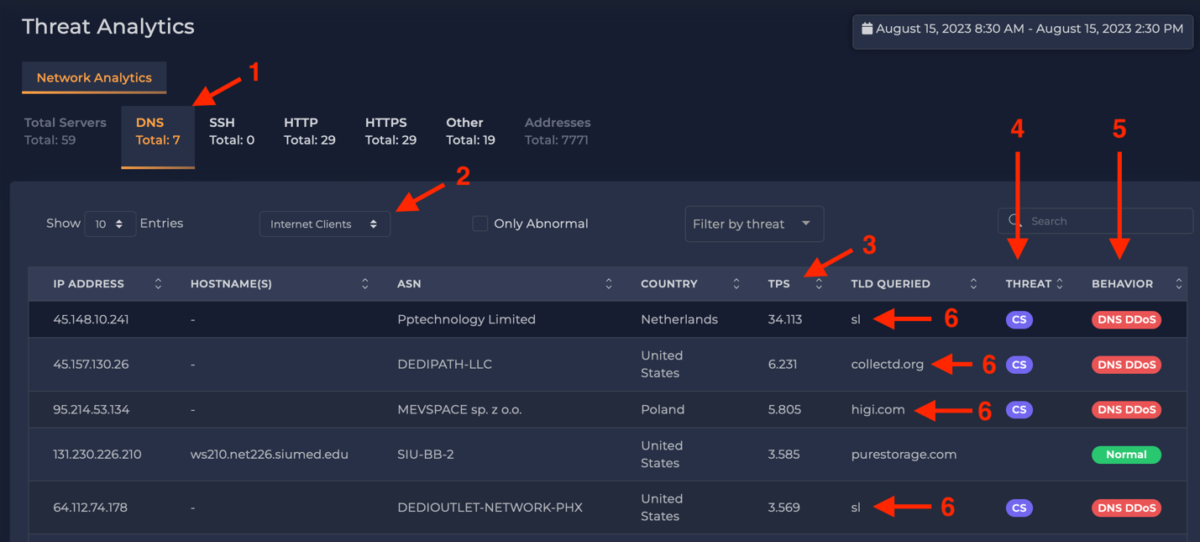
Figure 1: Examples of DDoS via DNS.
2. DDoS Attacker or Victim?
While, initially, it looks like the Internet client addresses 45.148.10.241, 45.157.130.26, 95.214.53.134, and
64.112.74.178 are launching attacks against Enterprise A’s DNS servers, they are actually the victims.
A common attack pattern is for a DDoS-as-a-Service organization to take a payment to attack another
party. The DDoS-as-a-Service organization does not typically attack the victim directly. Instead, it co-opts
other computers on the Internet, using them to attack the victim. There are many ways this can be done, but one way is to get other organizations to flood the victim with DNS replies that the victim did not ask for.
In this approach, the DDoS-as-a-Service organization composes a DNS query to Enterprise A but inserts the victim’s IP address as the source address in the packet. This DNS query is sent to an intermediate organization such as Enterprise A’s DNS servers which collect the relevant information to respond to the query. Then, Enterprise A’s DNS server sends the DNS reply to the IP address in the query’s source field. Recall that the source address was forged; it is the address of the victim.
Enterprise A’s responses might not be voluminous enough to take out the victim by itself. It is likely that the
DDoS-as-a-Service organization is using many DNS servers around the Internet to attack the victim at the
same time.
3. Can this impact Enterprise A?
Enterprise A’s DNS servers experienced CPU load increase because of these queries. If the enterprise is logging DNS queries, such activity will certainly increase the storage requirements and possibly costs to collect and maintain these logs (and possibly analyze them as well using a third-party tool such as Splunk). If Enterprise A’s DNS servers are behind stateful firewalls, the firewalls may be creating states to track these queries, thus contributing to potential memory issues inside the firewall. Finally, legitimate query responses that were cached in the DNS server in case there were subsequent queries for the same information may be kicked out of the cache. This means the later queries will take longer to service since the responses are not in the cache.
4.Summary
DDoS-as-a-Service organizations are using Enterprise A’s DNS servers to attack other computers on the Internet. A strong indicator of this is high transaction rates for information not associated with the enterprise (e.g., querying for information for Sierra Leone (sl domain)). In the attacks observed in Fig. 1, in addition to the behavior of DDoS activity, many of these addresses were flagged by a Threat Intelligence feed. Enterprise A may incur significant costs due to these attacks, including increased DNS log storage and potentially other costs (e.g., if these logs are sent to Splunk) and decreased performance of the DNS servers; and this activity could potentially also impact a firewall’s memory usage if the firewall tries to maintain state for every DNS query. Most importantly, this issue will impact the reputation of Enterprise A as it will be flagged as being used to carry out large-scale DDoS attacks although it may not be involved in it; this may, in turn, increase the cyber-insurance premium of Enterprise A.









