
5G Home Internet Root-Cause Analysis (RCA) with Ennetix xVisor
June 30, 2024Situational Awareness is “the understanding of an environment and its elements, and how it changes concerning time and other factors. Situational Awareness is important for effective decision-making in many environments” [Wikipedia]. In the case of an IT infrastructure of an organization, the goal of Situational Awareness with Ennetix xVisor is to provide information on:
- What are the entities on the network?
- What behaviors does each entity exhibit (suggesting entity type)?
- Are any of these behaviors a concern
- Have any entities recently changed their behaviors? (see Situational Awareness: “You Know What You Know”).
If you are responsible for an enterprise network, or even a single Internet-facing computer, your systems are constantly being scanned, probed, and potentially used in attacks against other systems. This is the background noise of the Internet. Detecting whether you are under attack should not be your focus—you are under attack. What you need to determine is (1) whether your systems have been compromised and (2) whether the nature of the attacks has changed. If a compromise occurs, you know the steps to take. However, if the nature of the attacks significantly changes, you must remain vigilant, as attackers may have discovered new methods, and these shifts in tactics could disrupt normal operations. To address this issue, you must understand the baseline behavior of your network, its components, and even the attackers. The process of establishing these baselines and detecting deviations is called User and Entity Behavior Analytics (UEBA).
Nefarious cybersecurity activity was discovered by Ennetix xVisor at one of our clients in the Midwestern US (hereafter referred to as ORG). This attack occurred over the Memorial Day long weekend, starting at 12:00 am (local time) on Saturday, and lasting about 72 hours! The attack got through ORG’s Firewall (a product from a well-known firewall vendor). The activity originated from a rogue nation, and the summary of the attack is below:
- Date range: May 26, 12 am, to May 28, 11 pm
- Internal SSH scanning (10.81.51.6)
- DDoS using ORG’s resources to attack others
- Badly-behaving DNS client (xxx.xxx.226.210)
- Three anomalous DNS query spikes received
- Multiple anomalous DNS query spikes made
Note that SSH scanning and DDoS leveraging DNS are common attack methods. However, establishing baselines for behaviors is very important and seems to be ignored by many organizations. Details on various situational awareness follow.
Internal SSH Scanning
Ennetix’s User-Entity Behavior Analytics (UEBA) algorithms, based on advanced AI/ML methods, detected “SSH Scan” as a major abnormal behavior. This Internal SSH Scanning activity persisted throughout the 72 hours. Figure 1 shows the details.
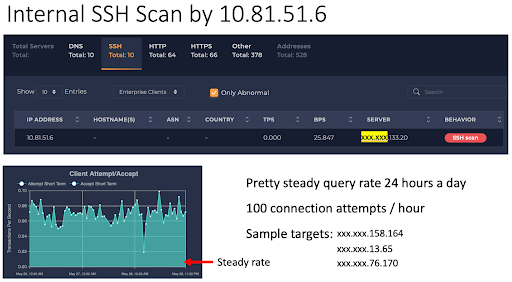
Fig. 1: Internal SSH Scanning by 10.81.51.6.
Attackers Using ORG for DDoS and one Badly-Behaving DNS Client
Ennetix’s AI/ML algorithms for UEBA found numerous DNS DDoS behaviors, as shown in Fig. 2. The attackers were exploiting ORG’s high outgoing bandwidth to launch DNS DDoS attacks. One example was that the attackers used ORG to DDoS 193.35.18.51, a Data Center in Germany; and this was done through queries for SL (Sierra Leone) to ORG (see Fig.3).
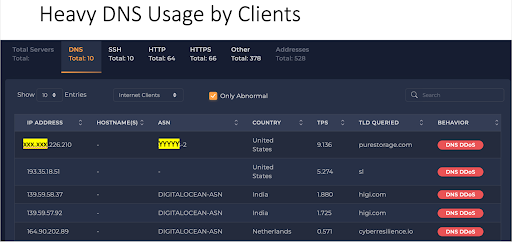
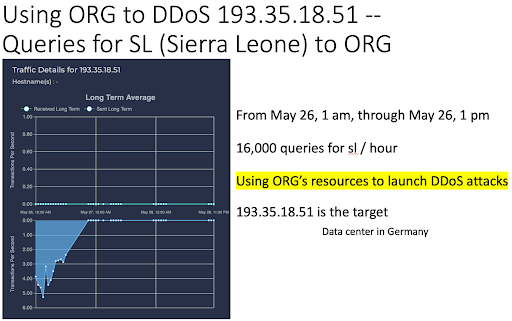
Fig. 2: Heavy DNS Usage by Clients (DNS DDoS attacks).
Fig. 3: Using ORG’s resources to DDoS 193.35.18.51.
Figure 4 shows the activities of a badly-behaving DNS client (xxx.xxx.226.210).
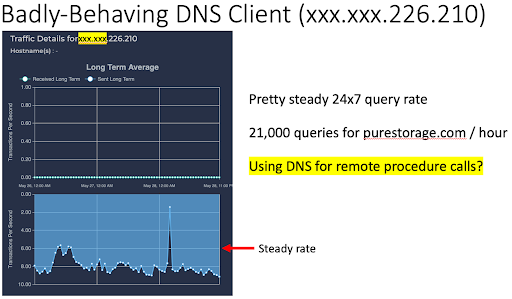
Fig. 4: Badly-Behaving DNS Client (xxx.xxx.226.210).
Anomalous DNS Queries
Three anomalous DNS query spikes were received during the 3-day weekend, as shown in Fig.5.
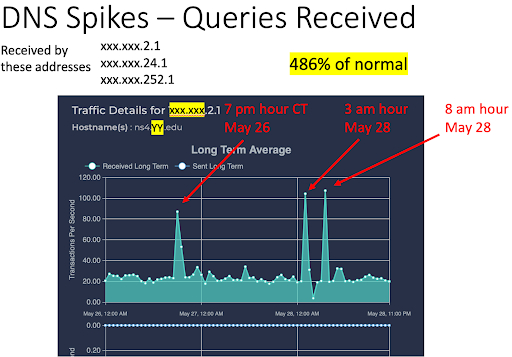
Fig. 5: Three DNS Spikes – Queries Received.
A huge number of DNS spikes were also seen for queries made (see Fig. 6).
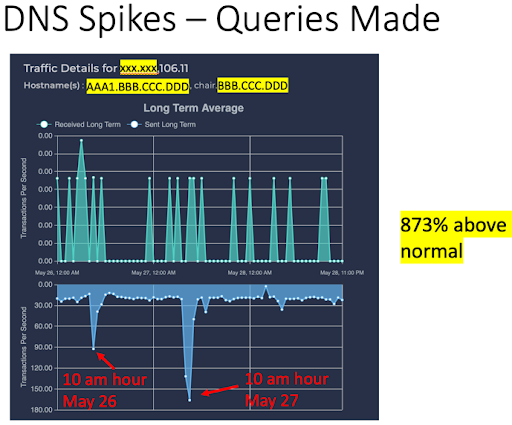
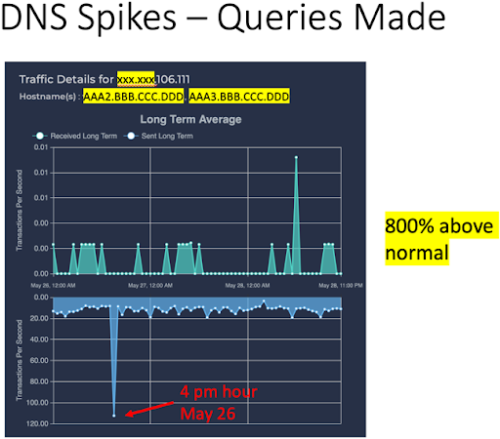
Conclusion
Situational Awareness with Ennetix xVisor can provide valuable information on an organization’s IT infrastructure. Nefarious activity was detected by Ennetix’s UEBA AI/ML algorithms in one of our client’s (ORG)’s IT infrastructure over the 3-day Memorial Day Long Weekend. The attack originated from a rogue nation and got through ORG’s firewall. The attack included Internal SSH scanning (10.81.51.6); DDoS using ORG’s resources to attack others; Badly behaving DNS client (xxx.xxx.226.210); Three anomalous DNS query spikes received; and Multiple anomalous DNS query spikes made. Note that SSH scanning and DDoS leveraging DNS are common attack methods. However, it is very important that organizations establish baselines for behaviors as they seem to be ignored frequently.
A few days later (not reported here) more hacking activity was detected from the same rogue nation, and this time they targeted ORG’s Medical Center, as well as many other hospitals and medical centers in the United States!
Further Information
For more information on Ennetix and its products/services and to read about our blogs, whitepapers, and literature, please visit https://ennetix.com.
For any questions, please email to info@ennetix.com.









