
xTend Your Visibility into Your Mac (or any Computer)
August 17, 2023Uncovering DNS DDoS Attack from an Adversarial Nation A Case Study on Threat Insights in Ennetix xVisor
DNS DDoS attack is one of the most prominent Distributed Denial of Service (DDoS) attacks targeting the DNS infrastructure of an organization. As the DNS system is responsible for all DNS queries (that translates all human-readable domains (e.g., www.example.com) into a corresponding server IP address) of an organization, attacking the DNS systems through DDoS can create a huge negative impact on the organization’s business activities. A common method of DDoS on DNS infrastructures is to flood the DNS servers with a large number of DNS queries and paralyze the DNS servers so that they cannot serve legitimate queries. This type of DNS DDoS attack is known as DNS flooding attack. DNS DDoS attacks are disruptive as a DNS system is critical to accessing online services and applications. Disrupting that will ultimately disrupt any online services provided by an organization. Many recent Internet outages happened due to DNS disruptions. Detection of DNS DDoS attacks is the first step in managing and mitigating such DDoS attacks, which are the most frequent on the Internet.
Situation
June 1, 2023, early morning hours at a large institution in Central USA:
Dozens of IP addresses from an adversarial nation made large numbers of DNS queries for names in the xxx.edu domain of the large institution.
How Ennetix xVisor Uncovered the Attack
Now let us focus on how Ennetix xVisor could uncover the attack using network logs and employing User Entity Behavior Analytics (UEBA) techniques. Ennetix xVisor keeps track of every network entity by utilizing various network activity logs and their relevant metrics and creating behavior profiles of all these network entities (such as DNS servers, DNS clients, etc.). These behavior profiles are then continuously analyzed to uncover abnormal behaviors on the network.
As shown in Figure 1, in this organization during the above period, dozens of IPs (DNS clients) from an adversarial nation made massive numbers of queries looking for names in the xxx.edu domain. Transactions per Second (TPS) from these IPs reach around 25 TPS. DNS queries from dozens of the adversarial nation’s IPs spiked at the same time (Figure 1). One specific IP was making 19,567 consecutive DNS queries for names in the xxx.edu domain.
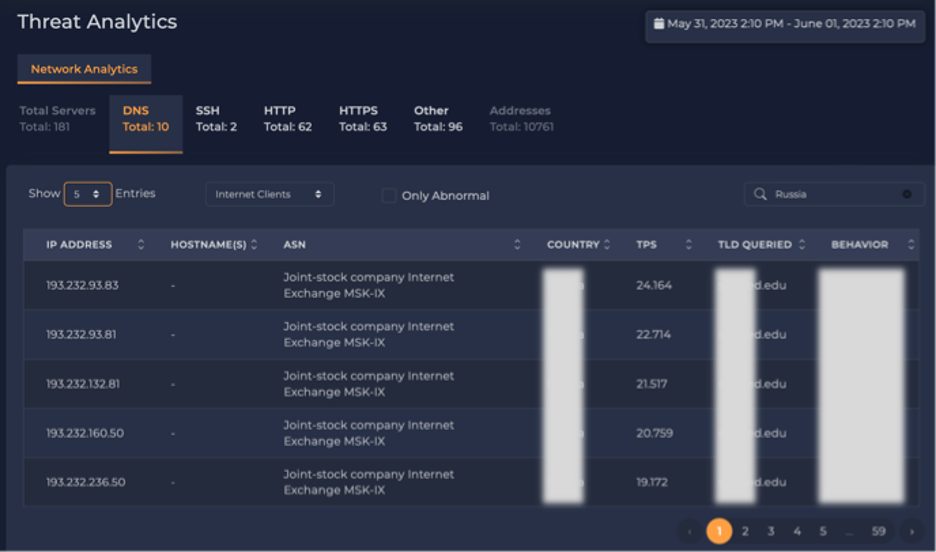
Figure 1: Abnormal DNS activities on the network.
As shown in Figure 2 (short time range view of 6 hours), the spike of DNS queries was at the 4-5 AM Central Time (CT) hour on June 1. The number of queries for the hour peaked at over 19,000 from a single IP address. Dozens of other IP addresses from the adversarial nation made thousands of queries each in that hour.
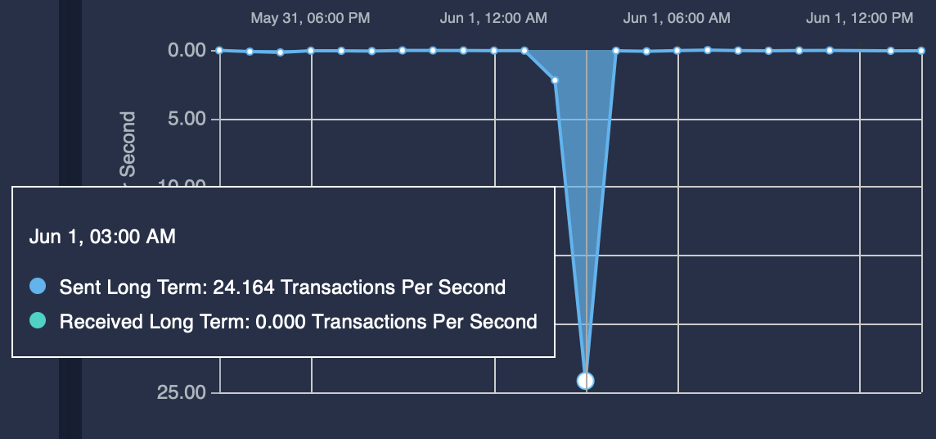
Figure 2: Spike from dozens of adversarial nation’s IPs at the same time.
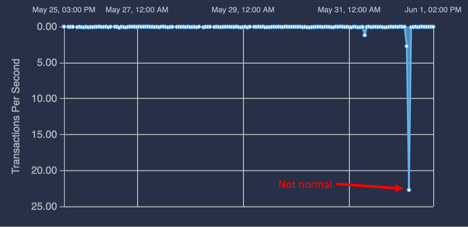
Figure 3: Query rate for the past week from one adversary IP.
Now, if we take a long-range view of transaction rates (Figure 3), it is obvious that the adversary IP never made any queries before during the past week. But, suddenly, during the hour of 4-5 AM CT, it was making a huge number of queries (Figure 3).
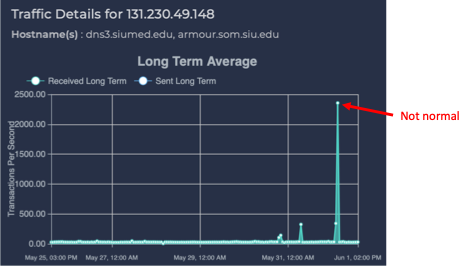
Figure 4: Query rate received by xxx.xxx.49.148 for the past week.
All these DNS queries were made against the DNS server with the IP address of xx.xx.49.148. That DNS server peaked at over 2,300 queries per second. If we look at the DNS queries received by xxx.xxx.49.148 for the past week (Figure 4), the spike is obvious during that hour. It looks to have handled about 2.6 million queries in that hour. That is about 7,000% above the normal rate. This presents a clear picture of a DNS DDoS attack on the DNS server with IP address xxx.xxx.49.148.
This case study presents important threat insights from a DNS DDoS attack as discovered by the Ennetix xVisor and its unique UEBA methods.
For more information, please contact us at info@ennetix.com.









