
Zen and the Art of AIOps for SMBs
September 1, 2023
AIOps: Is it a Destination?
September 5, 2023This series of blog posts is intended to capture some significant events and inventions that shaped the evolution of networks as they exist today. As an academician, researcher, and inventor, I have been a part of this evolution directly and a witness to many turning points. I will attempt to provide some perspectives along the way. We will begin this series with “Network Intrusion Detection”.
Part 1
Network Intrusion Detection System:
From First Implementation to Today’s AIOps Platforms
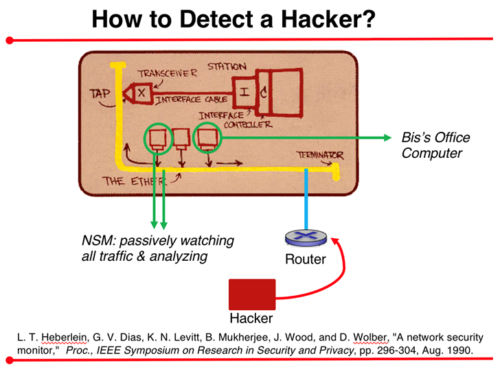
The first Network Intrusion Detection System (Network IDS), called Network Security Monitor (NSM), was designed and prototyped in the Computer Security Laboratory at the University of California, Davis, in 1989. It was built by graduate student Todd Heberlein, under the supervision of myself and Professor Karl Levitt. I presented this work for the first time at a leading computer security conference, the 1990 IEEE Symposium on Computer Security and Privacy.
 .
.
A brief history is in order. In Summer of 1988, the U.S. government – through the U.S. Air Force and Lawrence Livermore National Labs – gave Professor Levitt and me some funds to do “something about network security”! Professor Levitt had joined UC Davis in 1986 with expertise in computer systems, after a 20-year career at SRI International, while I joined UC Davis in 1987 as a fresh PhD graduate with background in computer networking, so we were an academic pair with complementary and synergistic expertise.
Those were days before wireless/cellular networks, and also before switched Ethernet. My first observation was that, if somebody (a Hacker) is breaking into my computer remotely, they must be coming over the broadcast Ethernet cable (see figure). Thus, by connecting another computer on the same Ethernet segment, and turning its Ethernet interface into promiscuous mode, we can observe all the bits (or, more specifically, the Ethernet frames) flowing on the cable. From this information, we could create the notion of TCP segments and connections, and “watch” all the underlying activities (as well as store and replay them as TCP sessions for later diagnosis). Note also that the network traffic was mainly unencrypted those days.
To detect intrusions, [our Network IDS (as well as other IDSs)] employed two types of approaches: (1) Misuse Detection (where misuse is a “tell-tale sign”—or “signature”—of an attack based on knowledge of prior attacks) and (2) Anomaly Detection (based on significant deviations from “normal behavior” as determined by statistical profiles). A Network IDS is as good as the strengths of its misuse-detection database and its anomaly-detection engine.
Our Network IDS was preceded by the host-based Computer IDS conceived a few years earlier at SRI International by Dr. Dorothy Denning, Teresa Lunt, and their team. While the host-based IDS analyzed computer system logs, our Network IDS (NSM) was based on analyzing network traffic. As an immediate follow-on to NSM, our team built the Distributed Intrusion Detection System (DIDS), which combined network monitoring (of NSM) with host monitoring for a more powerful IDS.
Our first prototype of NSM, presented over 30 years back, showed how to design a Network IDS. Little did we know then that Network IDS would become a $10B industry.
While a Network IDS detects intrusions (by “passively watching” network traffic), an Intrusion Prevention System (IPS) can create rules, e.g., in a Firewall, to prevent an intruder to get through the periphery of an enterprise, home, or an appropriately-defined system. In a later blog item, we will review the creation of the first Intrusion Prevention System (IPS).
Over the past three decades, Network IDSs have become very powerful, as the databases for “Misuse Detection” have become more comprehensive and are continuing to evolve as new attacks are detected and analyzed. The “Anomaly Detection” engines are also becoming stronger, particularly due to the application of AIOps platforms to digest data from multiple diverse sources to learn about new attacks and their patterns. Several important and relevant characteristics are incorporated in xVisor, the AIOps platform from Ennetix. For more information, please visit https://ennetix.com
About the author
Prof. Dr. Bis Mukherjee, Founder and President, Ennetix (also Distinguished Professor, UC Davis); Ph.D., Electrical Engineering, University of Washington, Seattle; B.Tech. (Hons.), Electronics Engineering, Indian Institute of Technology, Kharagpur.
Acknowledged authority in pioneering network technologies for 35+ years. His pioneering contributions in the networking world include, first design/proposal/prototype for:
- Network Intrusion Detection System (1990)
- Firewall (1989)
- Dynamic bandwidth allocation for EPON/FTTH (2002)
- Optical-wireless integration (2007), now 5G Fronthaul
References
L. Todd Heberlein, Gihan V. Dias, Karl N. Levitt, Biswanath Mukherjee, Jeff Wood, and Dave Wolber, “A network security monitor,” Proc., 1990 Symposium on Research in Security and Privacy, pp. 296-304, Oakland, CA, May 1990.
Steven R. Snapp, James Brentano, Gihan V. Dias, Terrence L. Goan, L. Todd Heberlein, Calvin Ho, Karl N. Levitt, and Biswanath Mukherjee, “DIDS (Distributed Intrusion Detection System – Motivation, Architecture, and an Early Prototype,” Proc., 14th National Computer Security Conference (NCSC), Washington, DC, pp. 167-176, Oct. 1991. (Winner, Best Paper Award at NCSC 1991.)
Biswanath Mukherjee, L. Todd Heberlein, and Karl N. Levitt, “Network intrusion detection,” IEEE Network, vol. 8, no. 3, pp. 26-41, May/June 1994.












